Preprocess Security Logs
& Route to Any SIEM
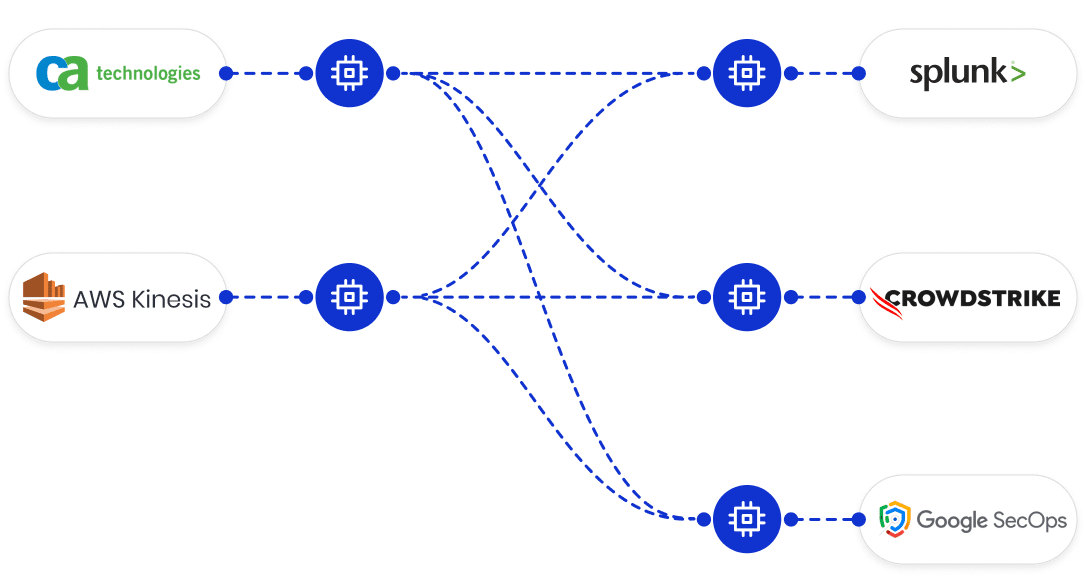
Chronosphere Telemetry Pipeline enables you to collect, pre-process, and route security logs from any source to any destination. As a result, you can reduce security information and event management (SIEM) software costs, enrich and normalize data in flight, and more easily meet compliance requirements.
Security Log Data Growth Slows Down Teams
Over the past year, organizations experienced 250% log data growth on average.
This level of telemetry growth creates several challenges for InfoSec teams:
Rising SIEM Costs Create Data Silos
It’s increasingly cost-prohibitive to centralize and retain large volumes of data in a SIEM tool. As a result, teams silo logs across data sources, SIEM endpoints, and storage targets, impacting both threat detection and investigations.
Additionally, short retention policies may cause teams to lose access to data needed to investigate a breach.
Poor Data Quality Slows Investigations
Security data comes in various formats from different sources. This inconsistency can make it harder to locate the information you need during an investigation.
Moreover, teams often lack contextual information that can speed up analysis, such as threat intelligence or environment asset tags.
How Chronosphere Helps Security Teams
From the creators of Fluent Bit and Calyptia, Chronosphere Telemetry Pipeline enables security teams to aggregate data from a wide-range of sources, unifying diverse information to enhance visibility.
Because Telemetry Pipeline processes data in flight, you can reduce noise, normalize, and add context to log data to speed up incident response. The Telemetry Pipeline data plane runs in your environment, enabling you to redact sensitive information before anything leaves your “four walls.”
Reduce SIEM Costs
Shrink the volume of data you ingest in your SIEM by filtering out low-value data and removing unneeded contents from your logs.
By reducing your security logging footprint, you also open capacity to aggregate data from more sources, including network devices, security appliances, applications, and cloud services.
Enrich and Normalize Data in Real Time
Add context to your logs to streamline investigations. Telemetry Pipeline provides an easy way to enrich data. Decorate logs with information from third-party sources, such as GeoIP or threat feed data.
Additionally, you gain a central location to normalize data from many different sources, helping you more easily locate the data you need.
Meet Compliance Requirements
The Telemetry Pipeline data plane runs locally within your environment – no data ever resides in Chronosphere’s cloud environment. As a result, you can redact PII and other sensitive information from your logs before the data leaves your environment.
Telemetry Pipeline also enables you to archive security logs in low-cost storage, like Amazon S3, to ensure long-term retention. You can rehydrate this data as needed to support investigations and other needs.



